As we approach 2012, it is time to begin analyze what marketing trends will dominate next year and where businesses are intending to allocate their marketing budgets. A new related survey reveals that the big majority of businesses are only intends to increase or keep their future marketing budget as is.
StrongMail has released its annual online marketing survey examining what will be the prominent trends for 2012. 939 business executive from different sizes businesses (about 38% small, 30% medium, 32% big) have participated in the survey. Let’s try to figure out for which direction the marketing wind will blow in 2012:
Budget Will Grow Or Remain The Same
It seems that the online marketing budget of businesses will only grow bigger or will stay the same in 2012- 51% have indicated they are intending to increase their budget, 41% indicated they intend to keep it the same and only 8% indicated it will decrease.

Top Growing Programs Spending – Email and The Social Media
60% of the participants have stated they are planning to increase their email marketing budget next year, 55% says they will enlarge their social media marketing budget and 37% intends to increase their search and mobile (each) spending. I found this as very surprising as i thought that email marketing is a decreasing in popularity trend.
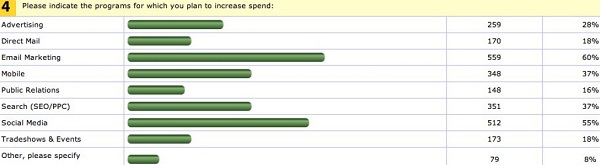
Specific Growing Budget Programs – Social Channels and Mobile Application
47% intends to increase email marketing budget in order to reinforce social channels, What can somehow explain the plans to increase email budget. 39% will increase their Facebook marketing budget and 29% planning to increase their mobile spending in order to build a mobile application.
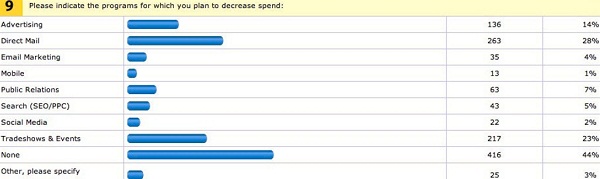
Top Decreasing Programs Spending – Direct Mailing, Tradeshows and Events
It is very easy to see that businesses are intending to allocate more funds to online marketing programs on the expense of offline marketing programs- 28% plans to decrease direct mailing budget and 23% intends to cut tradeshows and events spending.
Conclusion
The survey is pointing on very obvious trends in 2012- Online marketing channels budget will grow, in some of the cases on the expense of offline marketing channels where the leading fields are email, social media, search (SEO/PPC) and mobile. It is also important to emphasis that email spending will mostly rely on deeper integration with the social media.